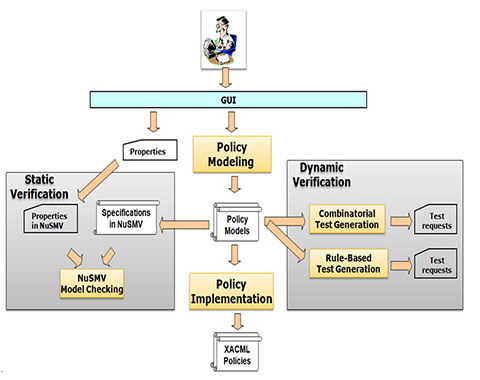
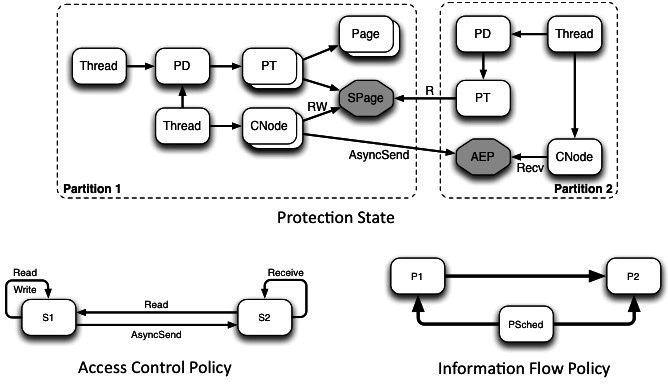
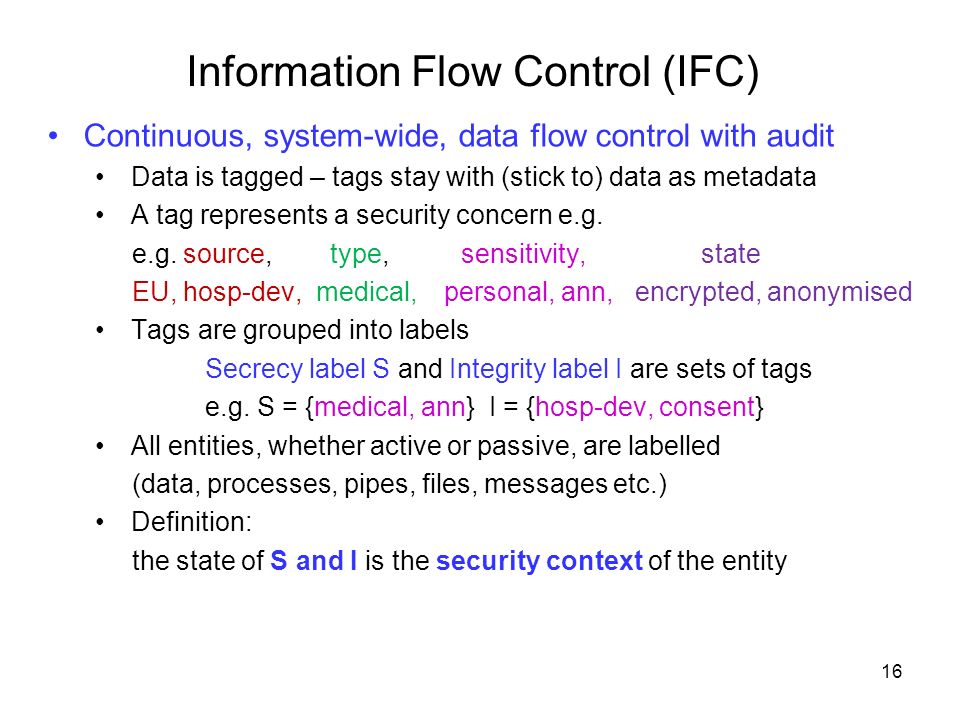
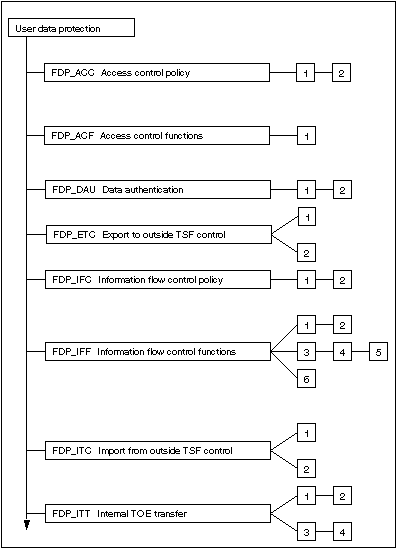
Information Flow Based Security Control Beyond RBAC: How to enable fine-grained security policy enforcement in business processes beyond limitations of role-based access control (RBAC) | SpringerLink
Defining an Information Flow Control Policy with Declassification and Countermeasures - Archive ouverte HAL

Method for tenants to jointly formulate information flow control strategy. | Download Scientific Diagram

The data flow diagram for an example of logic of the control policy... | Download Scientific Diagram

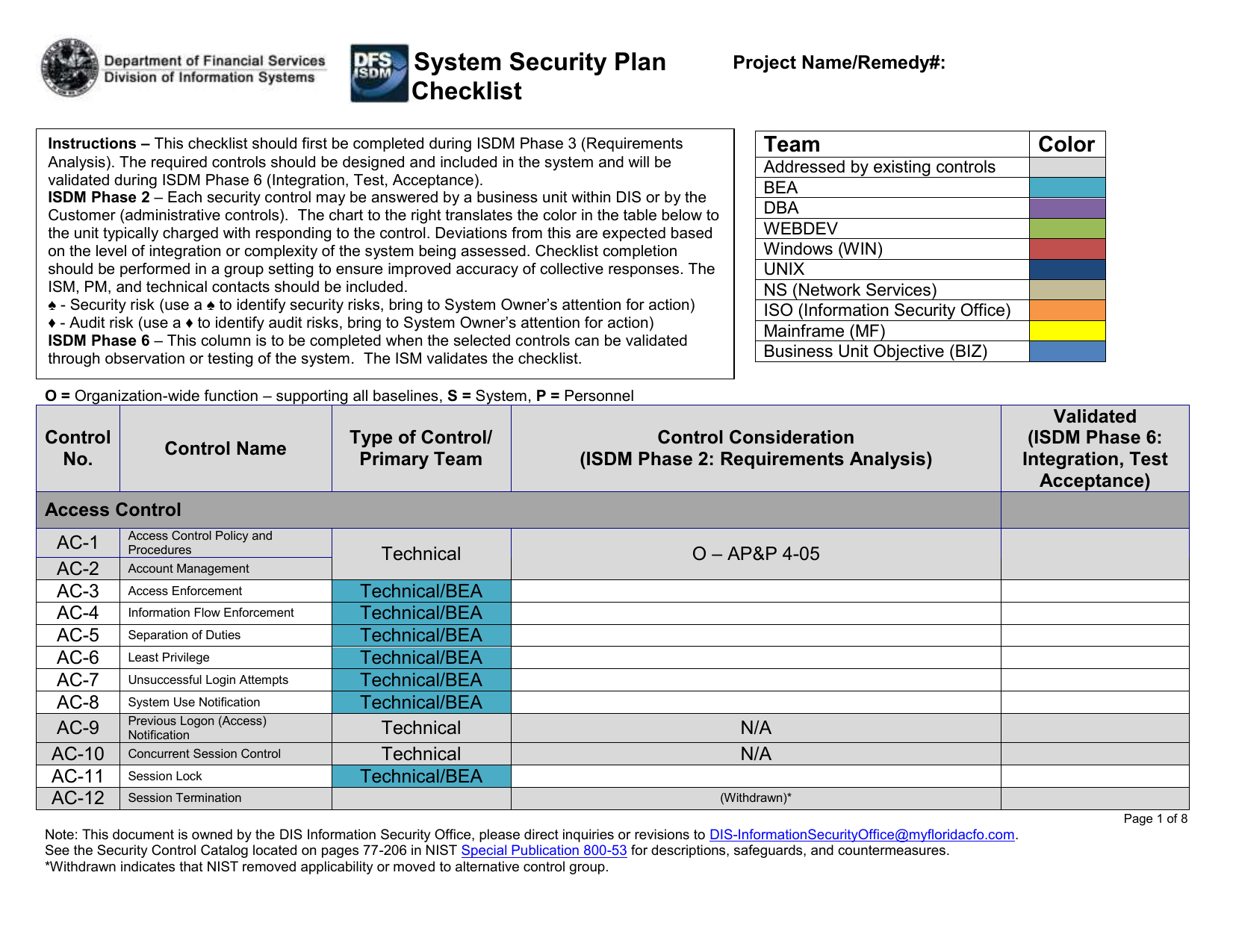
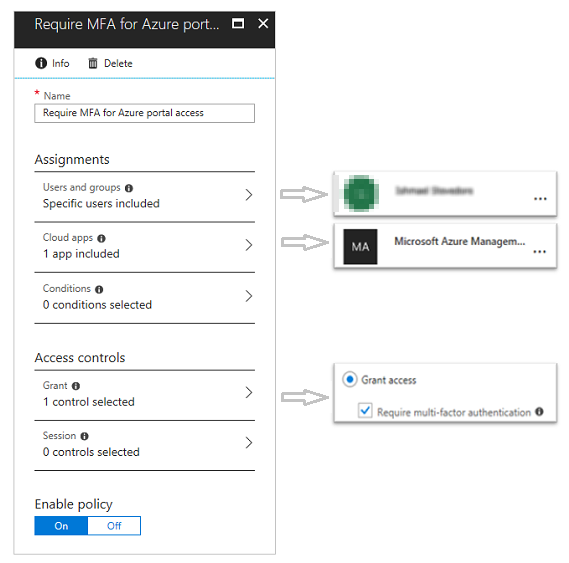
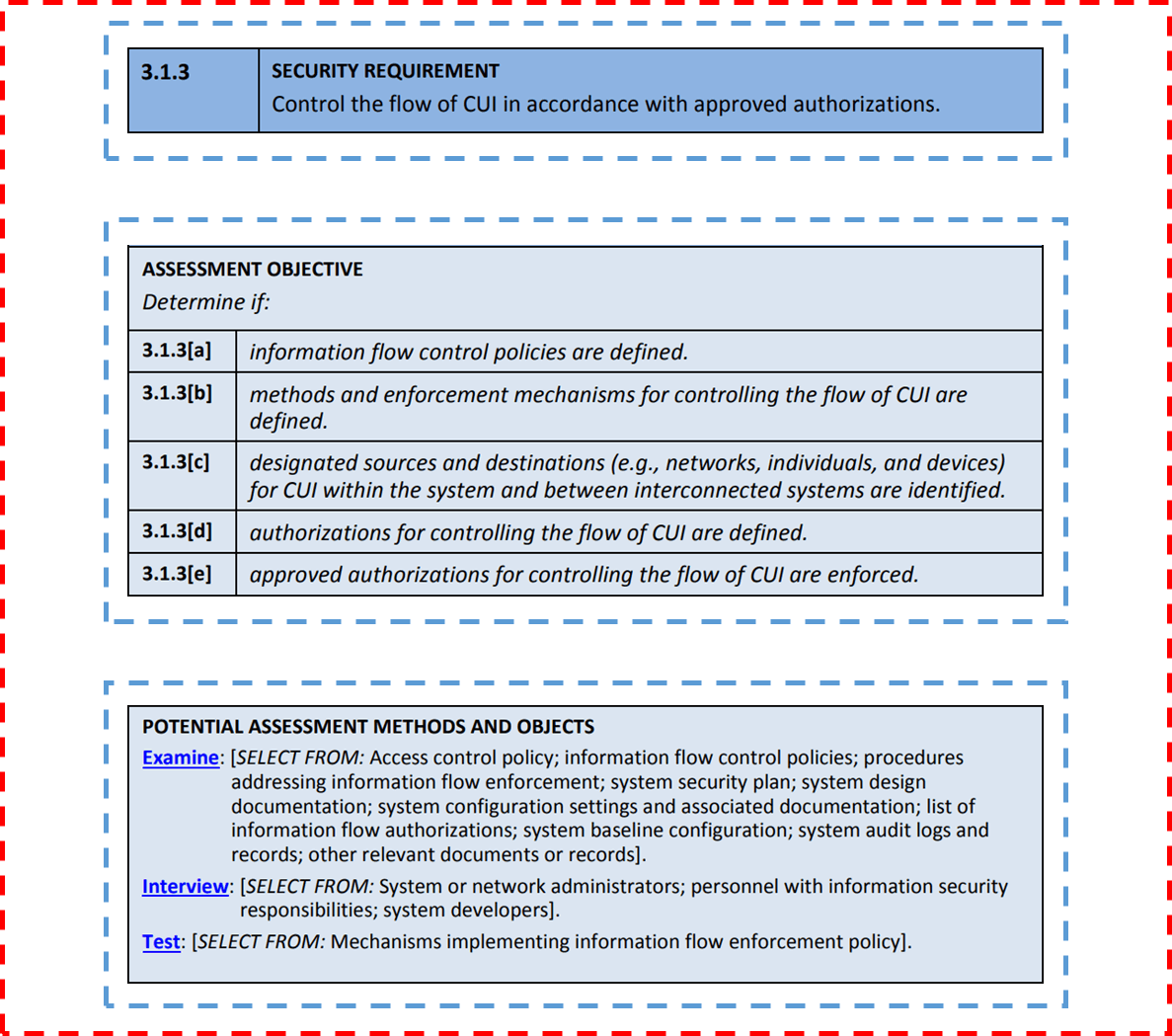
Chapter 7 Computer Security 1 Overview Important components of computer security: o User authentication – determine the identity of an individual accessing. - ppt download

Runtime Verification of Information flow: Policy-Based Runtime Verification of Information Flow Control: Sarrab, Mohamed Khalefa: 9783845432748: Amazon.com: Books
![Cisco SD-WAN Policies Configuration Guide, Cisco IOS XE Release 17.x - Policy Overview [Cisco SD-WAN] - Cisco Cisco SD-WAN Policies Configuration Guide, Cisco IOS XE Release 17.x - Policy Overview [Cisco SD-WAN] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/360001-370000/368001-369000/368414.jpg)
Cisco SD-WAN Policies Configuration Guide, Cisco IOS XE Release 17.x - Policy Overview [Cisco SD-WAN] - Cisco
![PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f5a30ed78c732463596bf2853bf596a79ecf08d3/23-Figure14-1.png)