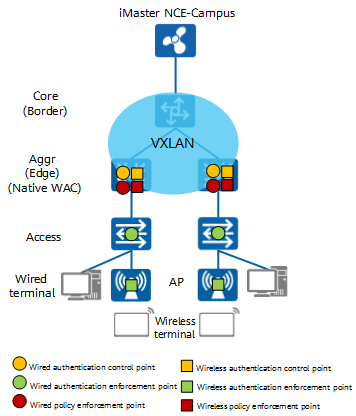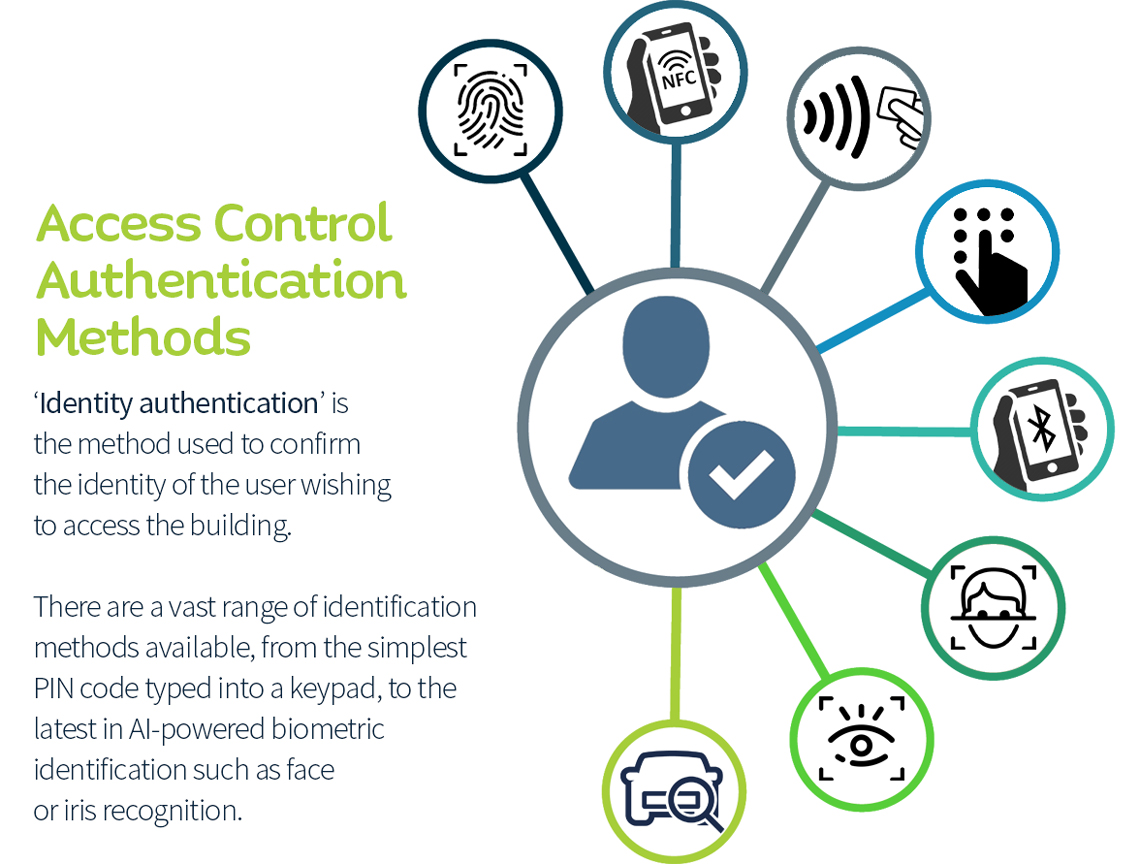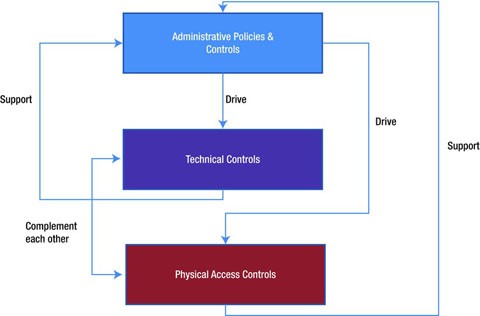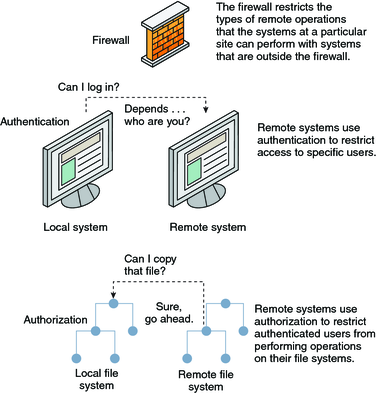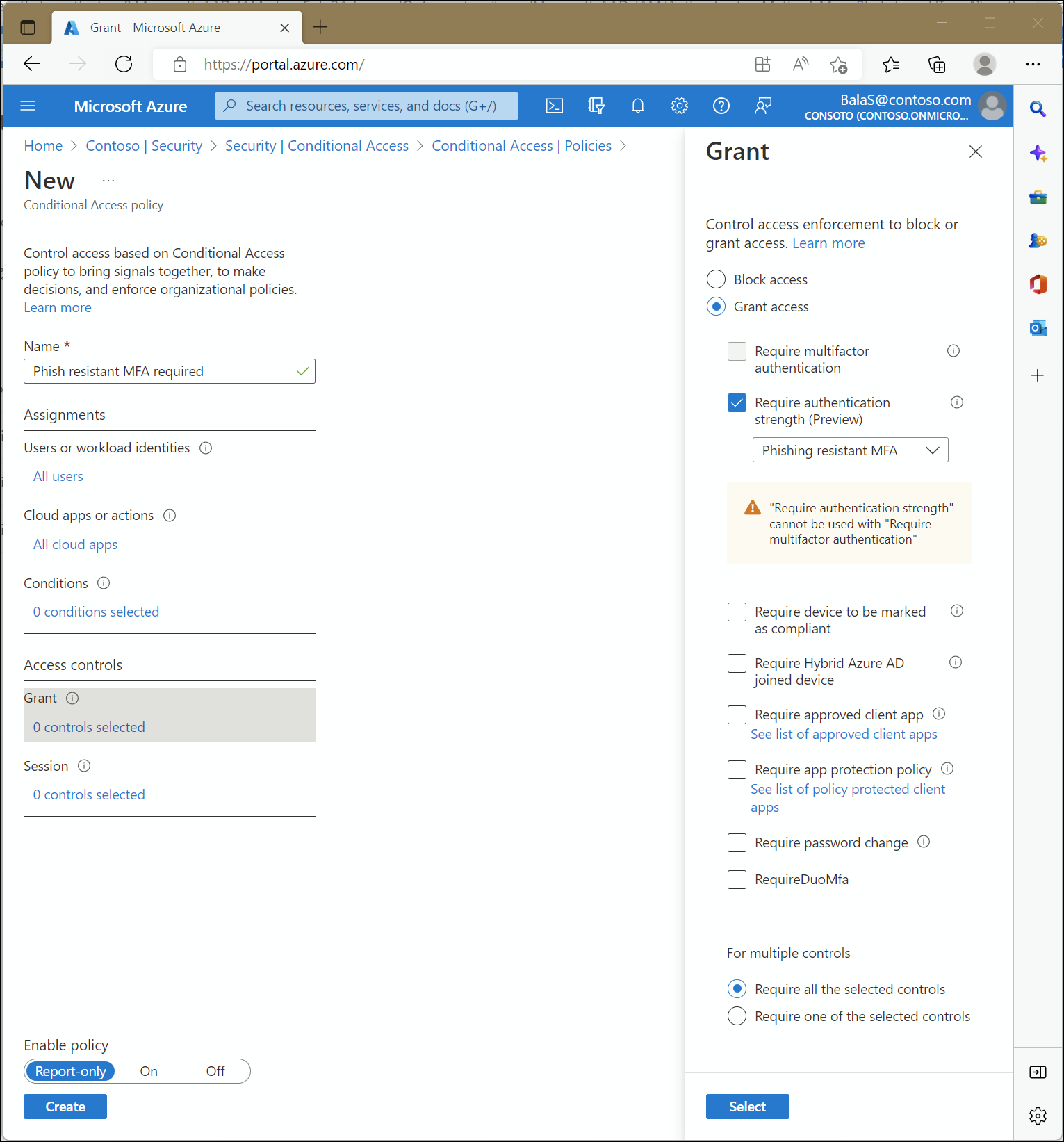
Overview of Azure Active Directory authentication strength (preview) - Microsoft Entra | Microsoft Learn

Sensors | Free Full-Text | Protocol-Based and Hybrid Access Control for the IoT: Approaches and Research Opportunities

Vulnerabilities in Single Sign-On services could be abused to bypass authentication controls | The Daily Swig

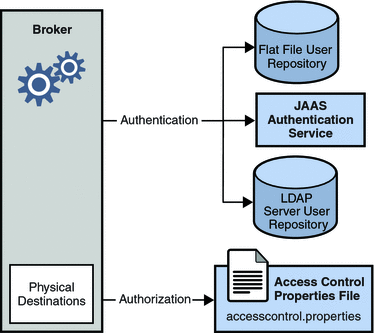
Cloud Security Considerations: Authentication / Access Control and Account Privileges - Accudata Systems
Authentication and Access Control Use Case Diagram for Cloud-based C4I... | Download Scientific Diagram