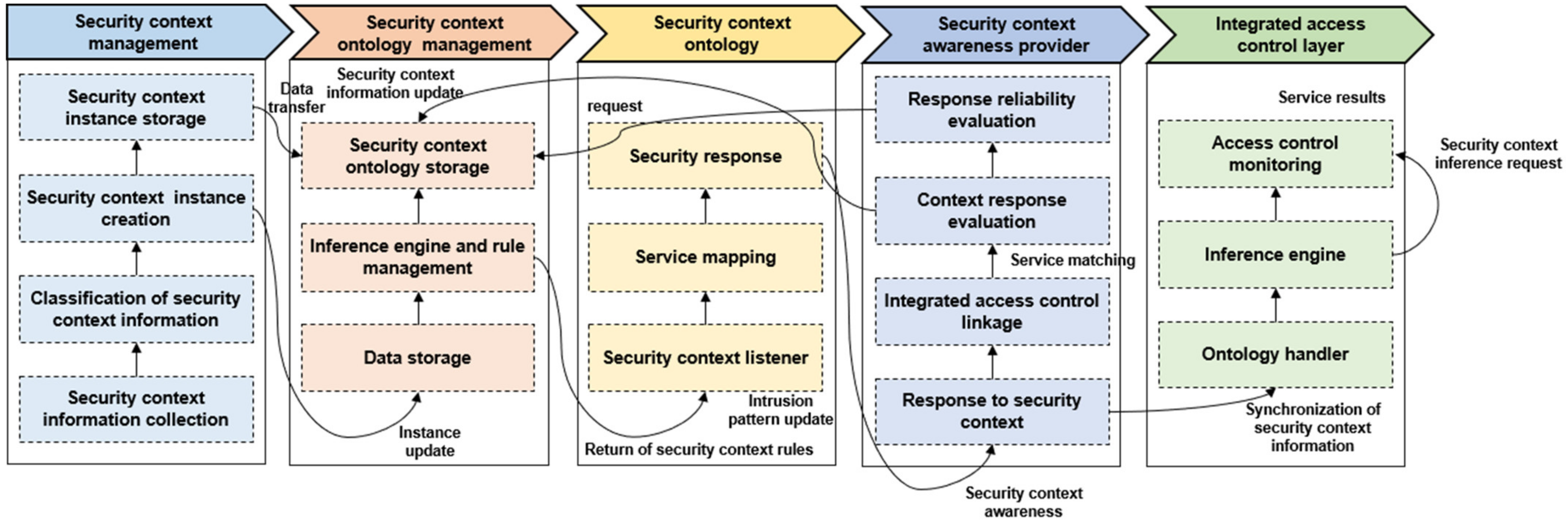
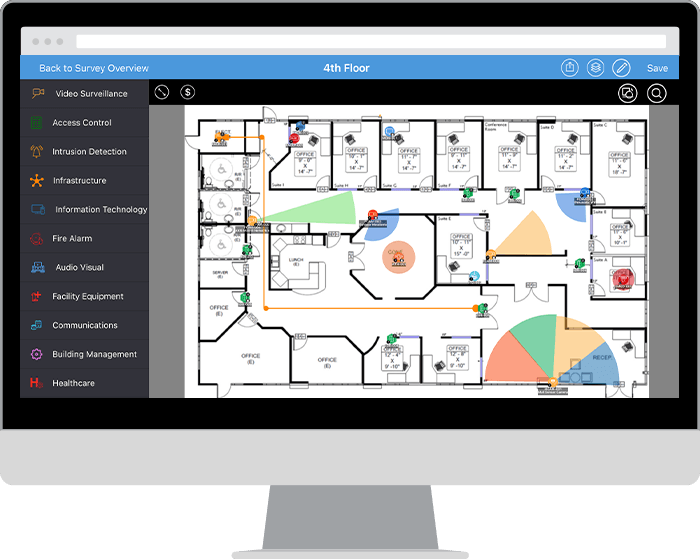
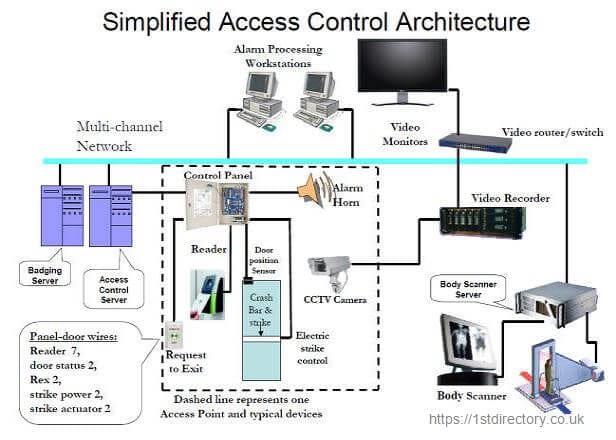
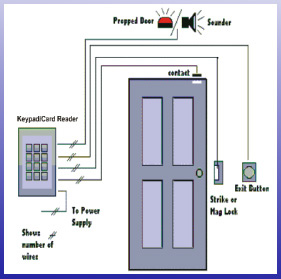
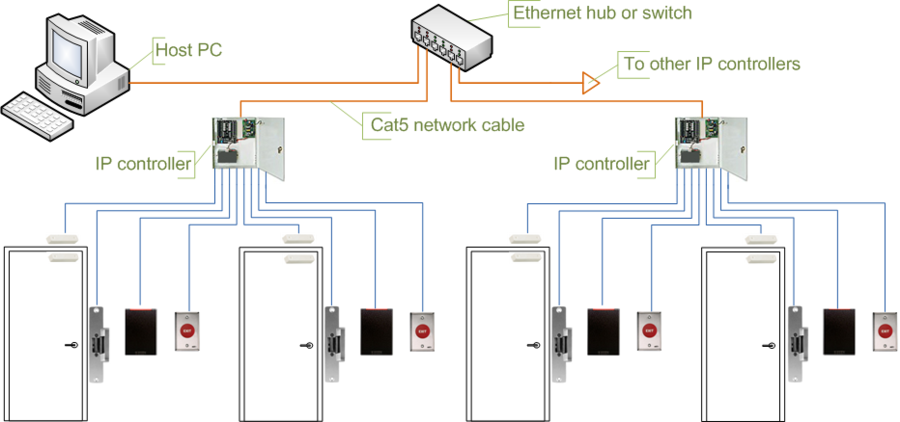
Access Control System Architecture Service in Sector 2, Noida, Idcube Identification Systems Private Limited | ID: 20842458555

Access Control Design - CloudCampus Solution V100R020C00 Design and Deployment Guide for Large- and Medium-Sized Campus Networks (Virtualization Scenario) - Huawei
Integrators Plus Services, LLC Video Surveillance, Intercom and Access Control Systems Sales, Design, and Installations. New York City, Rockland County, Westchester County, Orange County. Low Votage - Access Control Systems

Design and Implementation of Active Access Control System by Using NFC-based EAP-AKA Protocol | SpringerLink

How to design access control system for Saas application | by Anna Savytska | Muzli - Design Inspiration

Security System Design, Construction Site Protection, Authorized Access Control System Concept with Tiny People. Construction Stock Illustration - Illustration of password, scene: 219395122